Before i begin:(Yes yes, you might have seen it in HC.. but its a really well written tutorial that im really proud of)
While surfing on the net, i started reading about a relatively new malware type Called a Drive-By exploit, i did a research on it - watching LinkCabins videos, reading some webpages and viewing some White hat blogs and forums, and i was scared and surprised at the same time that we are ALL unprotected - i went up to Malware domain list and blade, viewing the websites that redicts you to a website which launches the exploit itself and downloads an unwanted program on the computer, scanning the program in virus total and the website itself showed me that the ratio detection was REALLY low, meaning that some websites were not detected by "Award winning Anti Viruses" and even more threatening that some of the malware wasn't detected.
What is a drive-by download?Well basically a Drive-By download is a download that occurs when a malicious website code exploits a vulnerability in various famous plug-ins such as: Java Script, Adobe Reader, Adobe Flash Player and uses it to download an unwanted program on your computer without your permission or of you being aware of it, most Anti-Viruses wont warn you about the download.
It would be important to mention that hackers hack legitimate websites and inject a code into them without the websites owner permission, the code should redict you to the website containing the Drive-By download.
http://www.youtube.com/watch?v=kMGNuw9c0SsTypical Black Hole Exploit kit behavior.
http://www.youtube.com/watch?v=YAesD1TEfk0In this case, the user had a special program to stop the exploit, as you can see his firewall didn't start up detecting the download, this happens because the Black Hole Exploit kid code is obfuscated and polymorphic which mutates the code, generating new variants each time which makes it undetectable.
It would be important to mention that not all downloads will download the program that this guy downloaded, i have no idea why the name was given to it but its not because of this program, i saw other videos where the exploit downloaded other malware into the computer.
Exploit kit types and their behavior:Well firstly, to build an exploit kit you have to be one rich motherfucker or either be really REALLY skilled, most hackers dont have time to look for them so they just buy them from other hackers, for example here is an advertising from the website DarKode.com, a website which containes many famous hackers(Paunch, bx1, carberp, alexudagov), in order to get invited to website you need to apply and show your "skills" and how you could contribute the forums so its not really easy but anyway - :
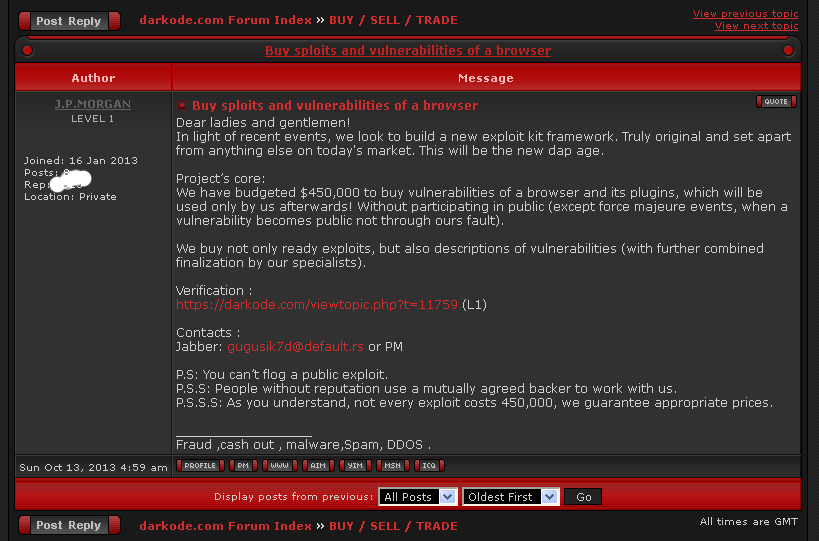 Black hole exploit kit
Black hole exploit kitThe exploit itself was released in 2012, in various Russian forums.
Black Hole Advertising(translated from a russian forum) -

The exploit was rather advanced, and worked like a botnet - by that i mean it would send the C&C server the details of the infected computer, and with what it was infected -

As you can see, this persons website was really wide spread, check out the hits he got.
The black hole is really dangours for its polymorphic code it generates new variants the mutates the code each time and the Anti-Viruses fail to detect it.
http://www.youtube.com/watch?v=D3NY5IBjMyMAs you can see, that was a legit website, that was hacked.
LinkCabin made a really nice presentation about the kit i would recommend watching it.
http://www.youtube.com/watch?v=EQ4AseeBVqMSo how to stay safe against the black hole exploit kit?
Well its pretty easy, while entering emails that you are not sure if they are so legit, put your mouse on the link and look at the website it redicts too, if the website doesn't seem legit dont enter it - most Black hole and other
Find a good host-based intrusion prevention system or HIPS but the safest thing you could do is removing the various plug ins like Java Script, Flash player and so on.
exploits websites would end int /index.html or /name.js or /name.pdf - from my research in malwaredomainslist.com.

- i know it leads to the Zeus Trojan download, but i was attempting to find various redict options.

Probably some exploit that tricks skids to think its some place where you can get various account passwords.

The Phoenix exploit that i would cover in a second.
Phoenix Exploit KitIntroduced by the famous hacker alexudakov that was arrested and then released (lmao he got arrested because of the kit and then came back to distributing it)
Andrey Anatolevich Alexandrov didnt really bother covering his tracks, maybe because he did not gave a shit, although he was married with a wife and a child.. but well you know if your a black hat you should learn form Andrey and while making epic exploits and malware you should cover your tracks.
Unlike the Black Hole Exploit the Phoenix Exploit targets mostly outdated plug ins, while the black hole almost each time updates to the new versions to remain undetected, the kit was selling for 2200 dollars a pop.. not really cheap.
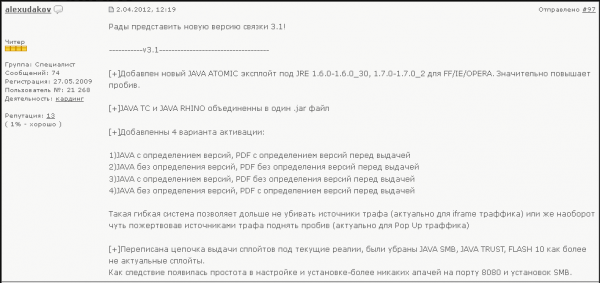
-
Phoenix Kit Advertising in exploits.in.
if you want to read about Andrey, there is some interesting information about him over here -
http://krebsonsecurity.com/2013/04/phoenix-exploit-kit-author-arrested-in-russia/ Well back to the exploit kit:
http://www.youtube.com/watch?v=KLUl0sUWUjoThe best video i could find, showing the Drive-By in action, as you can see it acts like the Black Hole, but what i found scary about the kit from looking at malwaredomainslist.com that MOST websites that redict to a Drive-By download are infected with the Phoenix Exploit kit.


-
How the phoenix kit is being sold and in which websites.

-Statistics, there is a picture that shows the country statistics but i think the thread has enough pictures.
How to stay safe against he Phoenix Exploit Kit:
Well i was searching through out the web and found a program that could deal with some Drive-By Downloads, i didn't test it out my self but be my guest its called ExploitShield.
http://www.youtube.com/watch?v=cN2CErkoiksBut it looks like the java.exe still downloaded itself into the computer so i don't really know if this is effective, but since the Phoenix Exploit Kit targets ONLY outdated versions of Flash player, java, and reader you should just update them and your safe.
Exploits in General and SummaryThere are WAAAAY more exploit kits than you think, i was looking through blade statistics page to only find out there are shit ton of free exploit kits that were used:

While the detection ratio was the following:

This picture shows that there is a chance of more than 50% than your AV wont detect the exploit kit.
Well thank you for your time, now you are safer on the internet, id like to thank XilyBot, for providing amazing information about the Black Exploit kit and The Phoenix Exploit kit, I would like thank LinkCabin for making those amazing videos on youtube!
Next time ill be posting a detailed thread about various botnets and their behavior.
And remember be safe, dont be stupid its always better to be safe than sorry.
here are the scan results from a phish email i just received:
https://www.virustotal.com/en/url/94804e1552d4b6deab1ab141b7de0644ea92ce7e6a92963020c4daad05e7a7b4/analysis/1393174873/As you can see, only 2 programs detected it as a Malware website.
[UPDATE]Use Malware-Bytes Anti Exploit, it should protect you.